Dear Securitarians,
This has been a difficult time for Domain 2 of the Certified Information Systems Security Professional (CISSP) security domains, Asset Security. First it was Dasan GPON fiber modems being pwned and pwned again by rival botnets. Then the VPNFilter botnet had its’ way with popular consumer-grade routers and even though authorities managed to foil that particular group, things got so bad that the FBI turned into a paraphrase of “The IT Crowd” asking, “Have you tried turning the Internet off and on again?”.
In the past, I kvetched about IoT security being the bane of our future, but Bad Actors seem to have plenty of low hanging fruit in the things-we-thought-had-some-security-already department to bother with sensors, valves and lightbulbs. Why get complicated with breaking IoT to your botnet when there is so much more processing power in consumer-grade world? Despite that, I am still looking forward with trepidation to the day when the hacking of the IoT really takes off and so I’m looking for ways to make things not-so-bad.
Domain 2: Asset Security and Domain 8: Software and Development Security
Sometimes new developments address multiple security domains. Microsoft’s new Azure Sphere does just that. Azure Sphere is a three part initiative from Microsoft aimed at doing to the IoT market what Windows did for the desktop; become the de facto platform. Azure Sphere combines a new class of microcontroller, a new OS, and new cloud services; all three parts touting security as their centerpiece.
Competition has already been heating up the IoT security space with Amazon launching their IoT operating system a:FreeRTOS last year. Amazon’s goal is to tie an IoT OS to all of the cloud innovations that they already own, making IoT management possible on an enterprise scale. Amazon has half a dozen hardware manufacturers committed to supporting a:FreeRTOS and the fact that FreeRTOS, the OS used for Amazon’s branded version, is an open-source heavyweight in embedded operating systems makes this a strong offering, from a marketing perspective.
Google has not been idle either, developing the Google Cloud IoT and pushing the Android Things platform, starting far back in 2016, as the chosen OS for IoT devices. Adding to Google’s software offerings, hardware vendors NXP, Qualcomm and MediaTek have their own System on Module (SoM) architecture solutions in production to work with Google’s Smart IoT vision. Google seems to cover all three areas of IoT for hardware, cloud management and OS. Android is a universal front end from which developers can work and is currently the world’s largest app platform. Coupling the Android platform with an earlier start in the field and Google’s advantage in the IoT world is enormous.
‘Smart’ devices, with their wealth of applications running on Operating Systems like iOS, Android and various forms of Linux, are what consumers think of when we talk about IoT. Yet, the IoT ecosphere is immense and is exploding ever faster and farther every year. In addition to ‘smart’ things, the IoT also encompasses things that are so very small and basic that they have been simply dubbed ‘connected’. These are the devices that bring the installed IoT numbers into the billions. It is the connected devices that are piling up the yearly IoT increase into the ten digit range and have been thrown into the field with only a nod to security. It is down here, at the not-quite-smart end, that Microsoft has decided to setup base camp with Azure Sphere, starting at the very foundation of small computing and building in security from the dirt up.
The Guiding Principles
Azure Sphere starts with a set of core principles that Microsoft refers to as the Seven Properties of Highly Secure Devices.
| Property | Description | Implemented In |
| Hardware-based Root of Trust | Unforgeable cryptographic keys generated and protected by hardware. Physical countermeasures resist side-channel attacks. The device has a unique, unforgeable identity that is inseparable from the hardware. | Azure Sphere Certified MCUs |
| Small Trusted Computing Base | Private keys stored in a hardware-protected vault, inaccessible to software. Division of software into self-protecting layers. Most of the software used on the device is outside the trusted computing base. | Azure Sphere Certified MCUs |
| Defense in Depth | Multiple mitigations applied against each threat. Countermeasures mitigate the consequences of a successful attack on any one vector. The device is still protected if the security of one layer of device software is breached. | Azure Sphere OS |
| Compartmentalization | Hardware-enforced barriers between software components prevent a breach in one from propagating to others. A failure in one device component does not require a reboot of the entire device to return to operation. | Azure Sphere OS |
| Certificate-based Authentication | Signed certificate, proven by unforgeable cryptographic key, proves the device identity and authenticity. The device uses certificates instead of passwords for authentication. | Azure Sphere Security Service |
| Renewable Security | Renewal brings the device forward to a secure state and revokes compromised assets for known vulnerabilities or security breaches. The device software is updated automatically. | Azure Sphere Security Service |
| Failure Reporting | A software failure, such as a buffer overrun induced by an attacker probing security, is reported to cloud-based failure analysis system. The device reports failures to its manufacturer. | Azure Sphere Security Service |
These seven principles provide a template that hardware and software manufacturers are using to create devices that are difficult to attack, or disable. The principles are implemented in three parts; Azure Sphere Certified Microcontrollers; Azure Sphere OS; and the Azure Sphere Security Service. Each part addresses multiple layers of security and forms an ecosystem that starts at the hardware level and goes up to the cloud. Here is a bit about each one.
Azure Sphere Certified MCUs
At the hardware level is the microcontroller, or MCU. These MCUs are very much like the processor you find in many smart devices, like your phone, but more compact and with some additional differences. Each MCU has I/O circuits, a Cortex-M core for real-time processing, a Cortex-A processor for running applications, and has connectivity built into the chip itself. MCUs have been around for a few years with each generation being smaller. The first wave of Azure Sphere approved MCU chips rides the next wave of smallness and will have WiFi as the built-in connectivity. Later MCUs will have Ethernet, or both Ethernet and WiFi built-in.
So far this sounds like any other system on a module compressed into one chip, impressive but evolutionary not revolutionary. Microsoft then adds in the security magic. Each MCU incorporates an IP block, a silicon library given by Microsoft to the chip manufacturer that is built into the chip. This is what makes each MCU a unique device, similar to the MAC address on an Ethernet controller, but unspoofable (so they say). Adding some form of unique asset identity at the hardware layer sets the security foundation for everything that is piled on top of it.
Adding to security, the MCU also has a set of firewalls, built into the chip using Microsoft’s Pluton security subsystem, so breaking into one area of the chip means you can go no further. Here’s a blurry screenshot from Azure Sphere: Build 2018 that is somewhat helpful:
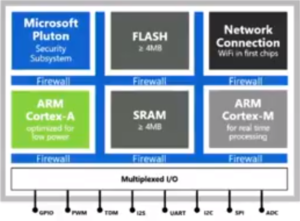
The IP Block, Pluton security subsystem and security architecture are licensed by Microsoft to the manufacturer royalty free in order to induce adoption.
The first Azure Sphere chip, the MediaTek MT3620, will come to market in volume this year. Followed by others, such as (as of 2018-06-01):
- ARM
- Hilscher
- LitePoint
- LongSys
- MediaTek
- Nordic
- Nuvoton
- NXP
- Qualcomm
- Seeed Studio
- Silicon Labs
- STMicroelectronics
- Toshiba
- VeriSilicon
Azure Sphere OS
This is where Microsoft will start to make its money. There are four software layers, on top of the hardware; the Security Monitor, the HLOS Kernel, the On-Chip Cloud Services and then come the application containers, one for each application.
- Security Monitor – like a hypervisor, monitors security
- HLOS Kernel – a custom Linux kernel, yep Linux. Manufacturers can submit changes for addition to kernel so in that respect it is ‘open’.
- On-Chip Cloud Security Services – provides updates for OS and apps
- Containers – a real-time I/O sandbox for the Cortex-M, and one sandbox for each application running in the Cortex-A processor
No word on the cost of the OS, but if we go by Microsoft’s current byzantine licensing models it will require an advanced degree to figure out.
Azure Sphere Security Service
There are no passwords on a Azure Sphere device. All communication, authentication and permissions is provided by security certificates. This includes device-to-device and device-to-cloud communication. The Security Service does the following:
- Detects failures and reports them
- Does behavior monitoring on the device for anomalous behaviors
- Manages software updates to OS and apps
Managing security certificates looks to also be done through the Azure Sphere Security Service. No details on that yet, but there will be a charge of some sort I am sure. Visual Studio is what developers will use to create software that runs on Azure Sphere, leveraging a large pool of development software and skilled programmer folksies.
More Cloudy Microsoft Stuff
To pad it all out, Microsoft also has come out with a collection of cloud services that make managing bee-lee-ons of IoT devices a click-breeze; Azure IoT Central for overall management of devices, Azure IoT Hub for connecting to and provisioning devices and Azure IoT Edge for analytics. There are costs for all of these.
Some of the references used here:
- Secure and power the intelligent edge with Azure Sphere : Build 2018 – https://www.youtube.com/watch?v=yozSfPp_R3k
- Microsoft Azure Sphere Leadership Vision – https://www.youtube.com/watch?v=lki7HOOkFjU
- Janakiram @ Forbes – https://www.forbes.com/sites/janakirammsv/2018/04/23/azure-sphere-microsofts-ambitious-plan-to-own-the-next-generation-iot-devices/#39bcea95e642
- TechGenix – http://techgenix.com/microsoft-azure-sphere/
- Aspencore 2017 Embedded Markets Study – https://m.eet.com/media/1246048/2017-embedded-market-study.pdf
The Wrap
Azure Sphere should be named Azure Ecosphere. You go all in or you pick another playground. From chip to OS to cloud, it is all Microsoft, there is little mix and match. If this makes you nervous, by all means look at one of the other biggies, or puzzle together your own security whole cloth solution for IoT. But remember that IP block? The one buried in the chip itself? That is the foundation for asset identity, upon which all else depends, and no one else is doing that yet for IoT devices. Remember up at the top of this very long-winded post about the “Hardware-based Root of Trust”? That’s what is required to build something more secure for IoT devices and that is where Azure Sphere shines. We shall see how many are lured by the shininess.



